Pietro Borrello
Microarchitecture Security Researcher
Apple SEAR
Biography
I am a Microarchitecture Security Researcher at Apple SEAR.
I received my PhD at the Sapienza University of Rome, working on Systems Security with a focus on applying Fuzzing and Program Analysis techniques to find and mitigate architectural and microarchitectural vulnerabilities.
In my PhD Thesis, I contributed to find and mitigate over one hundred bugs in software, operating systems, and CPUs.
I am also a passionate CTF player focusing on exploitation and reverse-engineering with TRX and mhackeroni teams.
Co-founder of the DEFCON Group in Rome.
BlackHat & OffensiveCon speaker and Pwnie Award recipient:
- Best Desktop Bug for “ÆPIC Leak: Architecturally Leaking Uninitialized Data from the Microarchitecture”
- Most Innovative Research for “Custom Processing Unit: Tracing and Patching Intel Atom Microcode”
- Systems Security
- Microarchitectural Attacks & Defenses
- Side-Channels
- Program Analysis
- Fuzzing
-
PhD in Engineering in Computer Science, 2023
Sapienza University of Rome
-
MSc in Engineering in Computer Science, 2019
Sapienza University of Rome
-
BSc in Engineering in Computer Science, 2017
Sapienza University of Rome
Projects
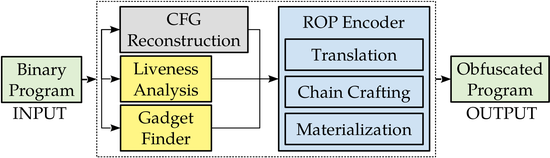
Custom Processing Unit
The first dynamic analysis framework for CPU microcode. Pwnie Award for Most Innovative Research
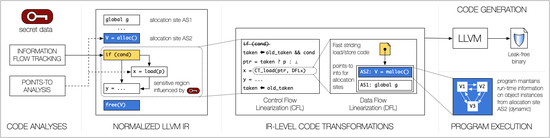
Constantine
A compiler-based system to automatically harden programs against microarchitectural side channels.
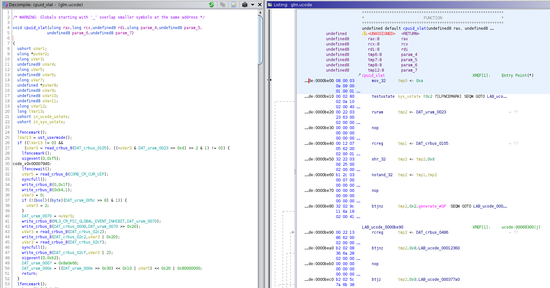
Intel Atom Microcode Decompiler
Ghidra Processor Module to disassemble and decompile x86 Intel Atom microcode.
Publications
CVEs
use-after-free in HID:bigben in the Linux kernel |
|
use-after-free in HID:asus in the Linux kernel |
|
type confusion & heap OOB write in RDS in the Linux kernel |
|
type confusion in Realtime Scheduler in the Linux kernel |
|
type confusion in TUN/TAP in the Linux kernel |
|
type confusion in TLS in the Linux kernel |
|
type confusion in SCTP in the Linux kernel |
|
type confusion & NULL ptr deref in HID in the Linux kernel |
|
| information disclosure in Intel CPUs (ÆPIC Leak) | |
undefined behavior in protobuf-c |
|
DoS in solidity compiler |
|
integer overflow vulnerability in Harfbuzz |
|
undefined behavior in lzrip |
|
DoS in njs |
|
undefined behavior in stb |
|
invalid free in lrzip |
|
use-after-free in stb |
|
integer overflow vulnerability in stb |
|
DoS in matio |
|
integer overflow vulnerability in FFmpeg |
|
timing side-channel vulnerability in wolfSSL |